This article discusses setting up a virtual machine (VM) as a virtual private server (VPS) and accessing it using secure shell (SSH). This VM VPS can then be used to test configuration and software changes before deployment to a live VPS. A deployed VPS can usually be accessed using SSH, therefore using SSH into VPS running on a VM is good practice for a live situation. This test configuration should accurately reflect the live VPS, reducing mistakes when moving from test to production. This tutorial and guide shows how to set up a VirtualBox VM and access it via the SSH client PuTTY, replicating production world VPS access.
You should never test on live systems. Replicate the live system in a test environment. Use the test environment to try out new configurations and software. When happy with the changes deploy to the live system with confidence. Of course there is no guarantee that the changes to the live system will not cause problems. However, the chance of errors occurring is reduced. The test environment should be the same as the live systems so that changes have the same affect when deployed.
Using a VM is a good way to test a system without impacting a local machine. VirtualBox is a free application that can run VMs. This article uses VirtualBox to configure a VM as a test VPS.
A VPS running in the cloud can be replicated on a local machine using a VM. The first step is to create a local VM. Then on the local VM install the same OS as the one running on the live VPS.
Use Port Forwarding for the Test VPS Networking
By default port 22 is used for SSH, see a list of TCP and UDP port numbers in Wikipedia. VirtualBox can be configured to listen to a port on the host machine and forward any traffic for that port to a port on the VM. This is configured in the VM’s network settings.
To change the network settings the VM VPS must be powered off or suspended. Or save the machine state with the VirtualBox VM window’s File then Close menu option.
With the VM highlighted in the VirtualBox Manager click the Settings icon or use the Machine menu and select Settings.
Under Network the Adapter 1 tab is selected, the default virtual network adapter enabled for the VM VPS. Click Advanced then click the Port Forwarding button On the Port Forwarding Rules dialog click the Adds new port forwarding rule icon. Give the new rule a name, e.g. ssh rule, the protocol will be TCP, Host IP address is blank. Choose a Host Port such as 2222, Guest IP is blank and Guest Port will be 22. Click OK to create the new rule.
Leaving the IP addresses blank means that if the host or guest IPs change then rule will still work. The host port should not be in use by another application or service (see the the Wikipedia list for common uses of ports). While 2222 is used by some products it is easy to remember as it is simply the default port 22 written twice. Use any valid port number in the range 1025 to 65535.
Install the PuTTY Terminal Emulator
The application PuTTY is a terminal emulation program, it implements Telnet, SSH and other network protocols. PuTTY can be used for remote connections to Windows or Unix type machines, such as a Linux based VPS.
Using PuTTY to SSH into VPS Running on a VM
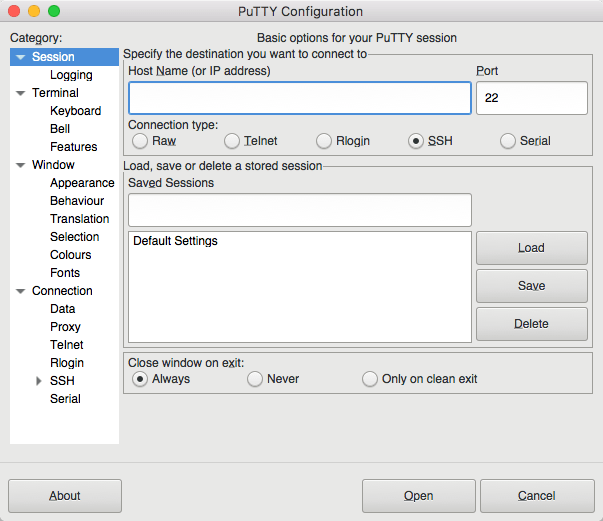
Open PuTTY, start a new session, the Hostname is localhost (your machine), which is the same as entering 127.0.0.1. The port is 2222, or whichever port number was set up in the port forwarding rule. Click the Open button.
The first time PuTTY connects to the VPS a security alert is shown. Confirm that the VPS is the valid by selecting Yes (it is running on the VM on the localhost). By selecting Yes the alert will not appear next time. A terminal window will appear and if everything is configured correctly the login prompt will be available. Log in as root with the password set during install. Run a command such as ls to list the files in the directory.
Typing logout will end the session and close the PuTTY window.
We now use FastSpring as our preferred storefront, you can pay with Credit / Debit Cards, PayPal, Amazon payments, Wire Transfer etc. etc. This store is very secure, simple and fast.
Purchase Putty 9.1.0 now and have Telnet SSH FTP SCP on your Mac made easy!